Archive for the ‘general tips’ Tag
Solving Puzzle Caches: Ciphers
Introduction
To read the previous post on Solving Puzzle Caches, go to https://bcaching.wordpress.com/2008/08/06/puzzles-part-2/.
There are many different types of ciphers from the simple to complex. Geocaching.com even uses a simple cipher for encrypting cache hints so that it is relatively easy to decode in the field. It is known as ROT-13 or the Caesar cipher with a shift of 13.
If you have a cipher on your hands, the first thing to do is determine what cipher you are dealing with. Hopefully the CO was kind enough to tell you or at least give you a hint. Most ciphers you will encounter on cache pages will be for letters only, so you will be deciphering into words. For example:
THE COORDINATES ARE NORTH FORTY DEGREES ZERO POINT FIVE THREE TWO
WEST SEVENTY FIVE DEGREES TWO POINT FIVE ZERO TWO
can be encoded into a variety of somewhat simple forms using monoalphabetic substitution ciphers:
Caesar with a shift of 3: (A=D, B=E, C=F, D=G, and so on)
WKH FRRUGLQDWHV DUH QRUWK IRUWB GHJUHHV CHUR SRLQW ILYH WKUHH WZR
ZHVW VHYHQWB ILYH GHJUHHV WZR SRLQW ILYH CHUR WZR
Caesar with a shift of 6: (A=G, B=H, C=I, D=J, and so on)
ZNK IUUXJOTGZKY GXK TUXZN LUXZE JKMXKKY FKXU VUOTZ LOBK ZNXKK ZCU
CKYZ YKBKTZE LOBK JKMXKKY ZCU VUOTZ LOBK FKXU ZCU
Atbash cipher, where the letters are reversed: (A=Z, B=Y, C=X, D=W, …)
GSV XLLIWRMZGVH ZIV MLIGS ULIGB WVTIVVH AVIL KLRMG UREV GSIVV GDL
DVHG HVEVMGB UREV WVTIVVH GDL KLRMG UREV AVIL GDL
Keyword ciphers are a little more complicated. They use a secret word or phrase that omits duplicates to come up with an alternately ordered alphabet. For example, if the secret phrase was LETS GO GEOCACHING, the translation key would be as follows:
ABCDEFGHIJKLMNOPQRSTUVWXYZ
LETSGOCAHINBDFJKMPQRUVWXYZ
“Geocaching” in the phrase changed to “cahin” to remove duplicate letters, then after the phrase all remaining letters are listed in order. The resulting cipher is:
RAG TJJPSHFLRGQ LPG FJPRA OJPRY SGCPGGQ ZGPJ KJHFR OHVG RAPGG RWJ
WGQR QGVGFRY OHVG SGCPGGQ RWJ KJHFR OHVG ZGPJ RWJ
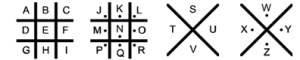
The PigPen or Masonic cipher is easy to spot. It uses a translation from letters into symbols:
which results in this:
What do you know?
If you know you’re dealing with a substitution cipher, but have no clue which one, you can always use the brute force method, and try a bunch of online tools to convert them. It can be more interesting to figure it out. If you expect to find numbers, write them out and look for repeating letters:
- THREE is a five letter word with two E’s. In the previous keyword cipher RAPGG is a possible candidate for “THREE”.
- SEVEN and SEVENTY repeats E in the 2nd and 4th positions. QGVGFRY repeats G in the 2nd 4th positions.
- COORDINATES is a relatively long 11 letter word that shows up surprisingly often in geocache ciphers and it has O repeated in the 2nd and 3rd positions so it can be easy to spot.
Once you determine a few of the letters this way it doesn’t take much more to decode the entire message.
Steganography
The art and science of writing hidden messages in such a way that no one apart from the sender and intended recipient even realizes there is a hidden message.
Is there an excessive amount of text information on the cache page? Does some of it seem extraneous or not even make sense? It may be hiding the real message. Look for a hidden message in the first letter or last letter of each word, every other word, or every word at the beginning of a sentence
Geocache On! No one really trusts hints from iffy finders. Trust yourself. Maybe eat treats every rainy Sunday.
What?? The first letters of each word spells: Go North fifty meters.
In other cases, you may need to count the number of letters in each word or sentence, or each word in a sentence to get the numbers you need.
Messages can also be hidden inside images so that they’re not visible without some manipulation. Try inverting images, or “Local Equalization” or “Find Edges” filters if available. The trouble with these is that a photo editor is needed like Adobe Photoshop or Corel Photopaint. There are some free tools that don’t offer as many functions but still may be helpful:
- Paint.Net (for Windows) at http://www.getpaint.net/ along with the BoltBait plugin pack that includes a steganography tool!
- SplashUp (online tool) at http://www.splashup.com/splashup/
That’s easy, what else have you got?
Polyalphabetic substitution ciphers are those that have changing substitutions throughout the cipher. A might translate to C one time, and T the next.
The Vigenère cipher is a popular one that uses a repeating keyword or phrase along with “tabula recta”:

Using this table is relatively straightforward once you’ve done it once or twice. To Encode, setup your message and your key on two separate lines (as shown below). The key repeats when it gets to the end – until there is a letter from the key that matches up with ever letter from the message. Then you take each two matching letters from the message and key, starting with “T” and “L” in this case, and find where they intersect in the table. Locating T across the top, and L along the left side, they intersect in the middle with “E”.
THE COORDINATES ARE NORTH FORTY DEGREES ZERO POINT FIVE THREE TWO WEST SEVENTY FIVE DEGREES TWO POINT FIVE ZERO TWO LET SGOGEOCACHI NGL ETSGO GEOCA CHINGLE TSGO GEOCA CHIN GLETS GOG EOCA CHINGLE TSGO GEOCACH ING LETSG OGEO CACH ING ELX UUCXHWPAVLA NXP RHJZV LSFVY FLOEKPW SWXC VSWPT HPDR ZSVXW ZKU ASUT ULDRTEC YABS JIUTEGZ BJU ASBFZ TOZS BETV BJU THE COORDINATES ARE NORTH FORTY DEGREES ZERO POINT FIVE THREE TWO WEST SEVENTY FIVE DEGREES TWO POINT FIVE ZERO TWO
Decoding the cipher is a little different. Here you line up the key phrase over the cipher (you would have the 2nd and 3rd lines in the example above), starting with “L” and “E”. Locating the “L” along the left edge, then follow that line across into the table to find “E”. The letter at the top of the column the “E” is in is your next decoded letter, in this case “T”.
The AutoKey cipher (aka Autoclave) is similar except it uses a single letter or short phrase to start things off followed by the message itself:
THE COORDINATES ARE NORTH FORTY DEGREES ZERO POINT FIVE THREE TWO WEST SEVENTY FIVE DEGREES TWO POINT FIVE ZERO TWO MTH ECOORDINATE SAR ENORT HFORT YDEGREE SZER OPOIN TFIV ETHRE ETW OWES TSEVENT YFIV EDEGREE STW OPOIN TFIV EZER OTW FAL GQCFULVNTXW SRV RBFKA MTFKR BHKXVIW RDVF DDWVG YNDZ XAYVI XPK KAWL LWZZRGR DNDZ HHKXVIW LPK DDWVG YNDZ DDVF HPK
Polygraphic Ciphers like Playfair, and Trifid are even more complicated. They encode two or more letters at the same time using a keyword or phrase. The encoded messages are much more difficult to break without knowing the key. They are usually written as two letter tuples. Using the same message and keyword as before, we get this using Playfair:
sa cb av hk ja do st th ms kn ps fr hk sx bt su tw tg wg kh ka oj sd oz ts
fy tw ts vc ec gs gt wl dl sr oz tb tl ms tg ex ak co dl jh wl wg kh ex av
and this using Trifid:
sejpcmqdrajunmsybil.crgabiwmsyexn.ymjwxrtbweuxre
onwbmkumfmlxrerqfezjjwlwyqwfzohkxmnanponxjqohqoe
Online Tools
There is a lot of information online about these ciphers and more. Here are some links to tools, including online converters, as well as lots of details about how the ciphers work. If all else fails, try wikipedia or google.
- http://sharkysoft.com/misc/vigenere/
- http://rumkin.com/tools/cipher/
- http://www.braingle.com/brainteasers/codes/index.php
- http://www.secretcodebreaker.com/codes.html
- http://www.simonsingh.net/The_Black_Chamber/pigpenWithMenu.html
- http://www.trincoll.edu/depts/cpsc/cryptography/substitution.html
Conclusion
There are many ways to hide instuctions or coordinates in geocache puzzles and hopefully this series helps introduce some of those techniques. Perhaps it will even inspire a few new puzzles!
Solving Puzzle Caches: Codes
Introduction
To read the previous post on Solving Puzzle Caches, go to https://bcaching.wordpress.com/2008/08/05/puzzles-part-1/.
Common Codes and other Languages
Numbers can be expressed in many ways. Here are a few common ones:
- Morse Code: http://en.wikipedia.org/wiki/Morse_code
0 = —–, 1 = •—-, 2 = ••—, 3 = •••–, … - Greek numerals: http://en.wikipedia.org/wiki/Greek_numerals
1 = αʹ, 2 = βʹ, 3 = γʹ, 4 = δʹ, 5 = εʹ, 6 =ϝʹ, ϛʹ or στʹ, … - Roman numerals: http://en.wikipedia.org/wiki/Roman_numerals
1 = I, 5 = V, 10 = X, 50 = L, 100 = C, 500 = D, 1000 = M
- Chinese numerals: http://en.wikipedia.org/wiki/Chinese_numerals
0 = 〇, 1 = 一, 2 = 二, 3 = 三, 4 = 四, 5 = 五, 6 = 六, … - Mayan numeral symbols: http://en.wikipedia.org/wiki/Mayan_numerals
If you want to see how many ways numbers are represented in a “few” different languages, check out the numbers from 1 to 10 in over 5000 languages here: http://www.zompist.com/numbers.shtml
Computer Codes
There are a variety of computer and Internet codes that are popular among puzzle cache hiders. If you’ve never seen a code before, it can be difficult to know where to start. The secret is to become familiar with different codes and know where to go to convert them to readable or “printable” text.
Printable text on computers is represented by numbers that are known as ASCII code. For a complete chart, see http://en.wikipedia.org/wiki/Ascii#ASCII_printable_characters.
“0” = 48 , “1” = 49, “2” = 50, …, “9” = 57, “A” = 65, “B” = 66, “C” = 67, …, “Z” = 90
Other codes like Binary (Base 2), Octal (Base 8 ) and Hex (Base 16) are just alternate representations of those ASCII codes (which are listed in decimal / base 10 above)
Here is the same set of coordinates represented using several codes.
Printable Text
N 40 00.532 W 075 02.502
ASCII Codes in Decimal / Base 10
78;52;48;32;48;48;46;53;51;50;32;87;48;55;53;32;48;50;46;53;48;50
Binary / Base 2
The numbers 0 and 1 only – the native language of modern computers.
01001110 00100000 00110100 00110000 00100000 00110000 00110000 00101110 00110101 00110011 00110010 00100000 01010111 00100000 00110000 00110111 00110101 00100000 00110000 00110010 00101110 00110101 00110000 00110010
Octal / Base 8
The numbers 0 through 7
116040064060040060060056065063062040127040060067 065040060062056065060062
Hexadecimal / Base 16
Hex for short. The numbers 0 – 9 and also the letters A, B, C, D, E, and F
4E2034302030302E3533322057203037352030322E35303200
MIME / Base 64
Normally used to encode non-text data like pictures or file attachments to a text form that can be included in email. This includes the upper case letters A – Z, lower case letters a – z, the numbers 0 – 9, and the symbols “+” and “/”. The symbol “=” also sometimes appears at the end.
TiA0MCAwMC41MzIgVyAwNzUgMDIuNTAy
Encoder / Decoder Tools
There are many online and offline resources for converting between different formats. Here are a few that I use most:
- http://www.nickciske.com/tools/ for converting between text and binary, octal, or hex
- http://base64-encoder-online.waraxe.us/ for converting between text and base64
- http://www.motobit.com/util/base64-decoder-encoder.asp – another base64 converter but this will let you convert images or other non-text data and save as a file
What’s Next
The next post will discuss ciphers. Check it out here: https://bcaching.wordpress.com/2008/08/08/puzzles-part-3/
Solving Puzzle Caches
Introduction
 A puzzle cache requires the finder to solve some type of puzzle at home or in the field to determine the actual hide coordinates. These listings usually start with a disclaimer indicating “The cache is not at the posted coordinates!“. The listed coordinates are usually within a few miles of the actual hide, but the puzzle must be solved to get the actual coordinates.
A puzzle cache requires the finder to solve some type of puzzle at home or in the field to determine the actual hide coordinates. These listings usually start with a disclaimer indicating “The cache is not at the posted coordinates!“. The listed coordinates are usually within a few miles of the actual hide, but the puzzle must be solved to get the actual coordinates.
Some puzzle caches do not have an at-home component and can be considered a field-puzzle or an advanced multicache. These require the finder to go to the listed coordinates and find some information in the field to solve the puzzle. This style of hide is sometimes also listed as a multicache.
Most puzzle caches have an at-home component that must be solved in order to determine the hide coordinates. After the puzzle is solved the coordinates lead directly to the hide, much like a traditional cache.
This post will focus on the at-home component of puzzle solving.
 Some of the at-home variety of puzzles provide complete instructions or are relatively straightforward, based on mainstream puzzles like Sudoku, crossword, word search, or logic. If so, just follow the instructions in the cache listing. If there are no instructions, or they are too vague, read on.
Some of the at-home variety of puzzles provide complete instructions or are relatively straightforward, based on mainstream puzzles like Sudoku, crossword, word search, or logic. If so, just follow the instructions in the cache listing. If there are no instructions, or they are too vague, read on.
What do you know?
There is a lot of information in a cache listing that the owner (or CO) has control over. He/she may choose to hide important clues throughout the listing so you should be aware of what to consider and what to ignore. The CO has control over the following:
- Name/Title
- Hidden by (this can be anything the CO chooses, not necessarily their official handle)
- Hidden on (the date can be set by the CO to any date in the past)
- Size, difficulty, and terrain
- Coordinates
- Cache description (including hidden text and hidden comments – more on this later)
- Images (background image, gallery, and in the description)
- Additional waypoints
- The hint
- Inventory (travel bugs, along with related images and logs)
- Logs
There is potentially lots of information and many times only little of it is needed since the most important parts of the listing are usually the name, description and hint but occasionally additional clues are sprinkled elsewhere. Unfortunately cache owners will often sprinkle bits of useless or misleading information to try to throw you off! As you learn and use different puzzle techniques it will become easier to recognize what is important and what is not.
When you are trying to solve an ambiguous puzzle or cryptogram, one of the most important things you know is often the listed coordinates. When a puzzle solution contains the entire set of coords (cardinal direction, degrees, minutes, decimal minutes). In that case you’re already one step ahead since you know the final coords have to be within a few miles of the listed coordinates. If the listed coordinates are N40 01.234 W74 54.321, it’s a safe bet that the puzzle solution will include 40, 74; 00, 01, or 02; and 53, 54, or 55 as numbers or spelled out as words. You might also be looking for North and West. Identifying where they exist in the puzzle solution can help you solve the rest of the puzzle.
Counting: Sometimes the coordinates are hidden as the number of letters in a series of words, or the number of words in a series of sentences.
What can you learn?
Many puzzles require you to go to the Internet to search for information needed to solve it. Wikipedia.org and Google.com are excellent resources that can be used to search for that information. The trick is sometimes figuring out what to search for. The cache description, hint, name of the cache listing, or even the “hidden by” will often hold clues about the technique you need to use to solve the puzzle.
Go to the source
 Text and comments can be hidden by the CO in the cache description. Sometimes, the can write white text on a white background making it invisible, however you may notice a suspicious blank area in the cache listing. A quick way to check for this is by using the “Select All” command in your browser. You can find the command in your browser’s Edit menu, or use the keyboard shortcut Ctrl-A. This will select the entire contents of the listing, including hidden text which will now be visible.
Text and comments can be hidden by the CO in the cache description. Sometimes, the can write white text on a white background making it invisible, however you may notice a suspicious blank area in the cache listing. A quick way to check for this is by using the “Select All” command in your browser. You can find the command in your browser’s Edit menu, or use the keyboard shortcut Ctrl-A. This will select the entire contents of the listing, including hidden text which will now be visible.
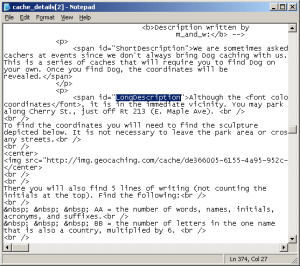
Another place to look is in the HTML source. This can be a little overwhelming for newbies, but try it and see. Select the “Source” command from the View menu (“Page Source” in Firefox). This will pop up a text editor window containing the HTML source for the page. Use the search function of your editor to find the text “LongDescription” without the quotes, no space between the words:
This will get you to the part of the listing written by the CO and you can scan through the text which should match closely to the actual cache description, but will also have HTML tags sprinkled here and there. HTML comments are preceded by the sequence “<!–” and end with “–>” and will sometimes have useful information hidden there by the CO.
Coordinate Formats
Geocaching.com lists coordinates in Degrees/Minutes/Decimal Minutes but there are other formats you should be aware of since puzzles will sometimes result in coordinates in an alternate format that must be converted to a form you can enter into your GPS.
Here is the same coordinates listed in multiple formats:
Degrees/Minutes/Decimal Minute:
N40 01.234 W74 54.321
Decimal Degrees:
40.020567, -74.905350 (S latitude and W longitude represented as negative) or N40.020567 W74.905350 (using cardinal directions)
Degrees/Minutes/Seconds:
N40 01 14, W74 54 19
UTM:
18T E 508077 N 4430044
An excellent tool for converting between formats is FizzyCalc (for Windows) at http://www.fizzymagic.net/Geocaching/FizzyCalc/index.html. A similar online tool for converting between formats is at http://boulter.com/gps/.
Confirming Solutions
Some cache listings provide a link to confirm coordinates, but others use methods like “Digital Root” or Sum of digits. FizzyCalc will calculate the Digital Root of a set of coordinates for you, but here’s how to do it by hand:
1. Add up all the individual digits in your solution coordinates. For example, the sum of the digits in N40 01.234 W75 43.210 are 4 + 1 + 2 + 3 + 4 + 7 + 5 + 4 + 3 + 2 + 1 = 36.
2. Add up all the individual digits in the previous sum. 3 + 6 = 9.
3. Repeat <2> until only one digit remains. The digital root in this example is 9.
If there is no mechanism provided in the cache listing to confirm your coordinates, there are a few more things you can do.
Look at a satellite view of the coordinates using http://maps.google.com. Correct coordinates should not be in somebody’s yard or on their roof, or in the middle of a street. Does the location appear to match the terrain rating? If GZ is an obviously wrong location go back to the drawing board.
If all else fails, send an email to the cache owner. Most cache owners will let you know if you are right or wrong and if they see you’ve spent some time on the puzzle they might even give you a free nudge in the right direction.
Stay Tuned
There’s more to come. Computer codes and cryptography are next.
 Comments (18)
Comments (18)